workflows:
- tag_query: prod
runs_on: "private-runner-production"
plan:
- type: run
cmd: ['${TERRATEAM_ROOT}/bin/policy-check']
ignore_errors: true
- type: init
- type: planTerrateam
What is Terrateam
Terrateam is an open-source solution for managing infrastructure with GitOps workflows.
Why Terrateam
Many engines (Terraform, Tofu, CDKTF, and more)
GitOps
Strong monorepo Support
Flexible configuration for complex environments
Scalable architecture
Supported Engines
Terraform/Tofu
CDKTF
Pulumi
Custom (anything with a Plan + Apply workflow)
GitOps
Product entirely configurable inside of the repository with multiple configurations co-existing.
Monorepo Support
Flexible
Terrateam Architecture
Terrateam from a User’s Perspective
Workflow Steps
- Developer → Open Pull Request
- Terrateam plan runs automatically
- Plan Output + Policy Feedback in PR (Security, RBAC)
- Wait for approvals
- Apply
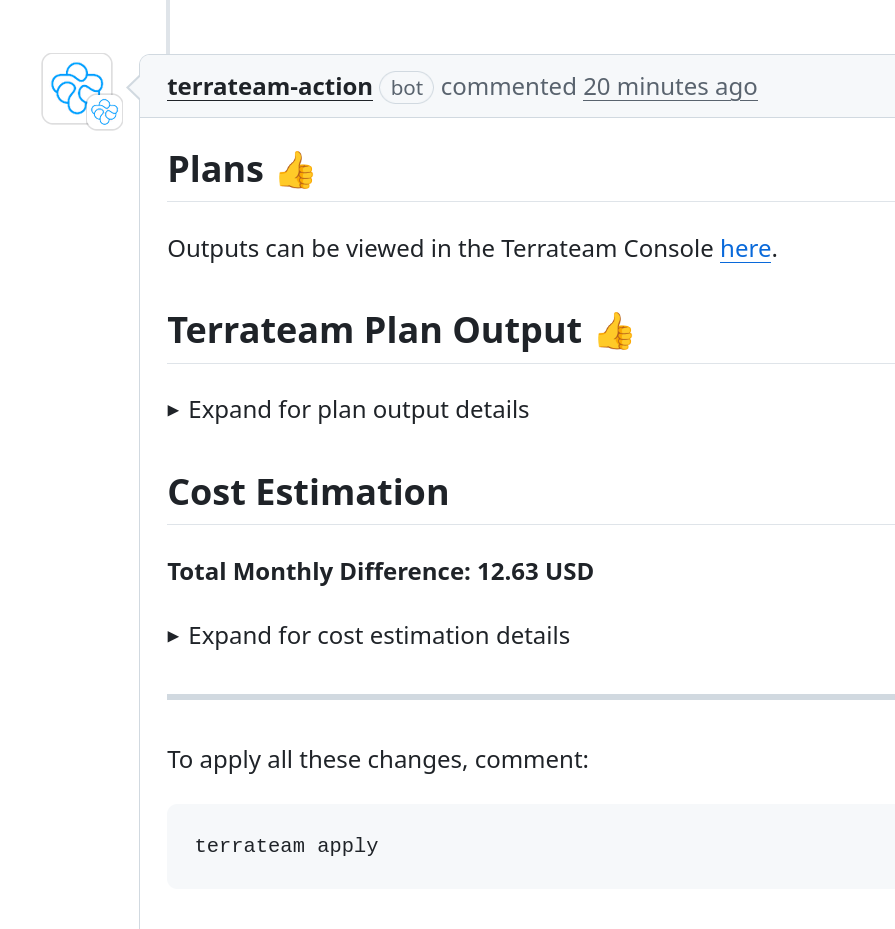
Terrateam UI Features
- Recent plans/applies
- Execution output
- Audit trail
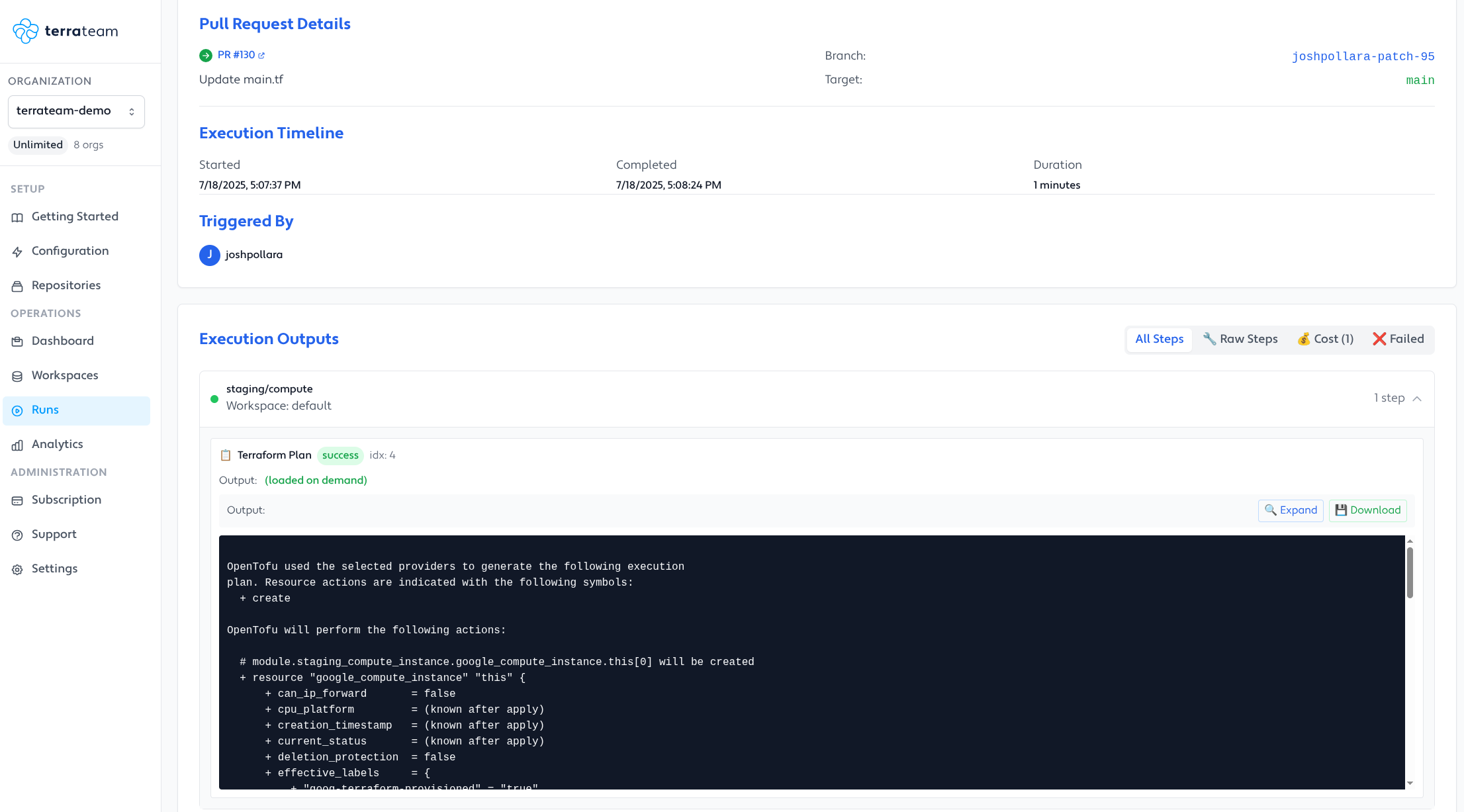
Example PRs (1)
Basic Plan & Apply: https://github.com/terrateam-demo/example-basic/pull/1
Layered Runs: https://github.com/terrateam-demo/example-layered-runs/pull/1
Gatekeeper: https://github.com/terrateam-demo/example-gatekeeper/pull/2
Example PRs (2)
Indexer: https://github.com/terrateam-demo/example-indexer/pull/1
RBAC + Apply Requirements: https://github.com/terrateam-demo/infrastructure/pull/54
Drift Detection: https://github.com/terrateam-demo/terraform/issues/188
Security: https://github.com/terrateam-demo/infrastructure/pull/60
Terrateam for Admins
Targeting: directory, workspace, tags, globs
Integrate any tool (CLI/API): OPA, Checkov, etc.
Per-team RBAC + apply requirements
Centralized config, federated execution
Private runners per environment
Example: Directory Configuration
dirs:
- production/app:
tags: ["prod", "app"]
- staging/**:
tags: ["staging"]Example: Workflows
workflows:
- tag_query: "staging"
plan:
- type: oidc
provider: gcp
service_account: "..."
- type: init
- type: plan
- tag_query: "production"
plan:
- type: oidc
provider: gcp
service_account: "..."
- type: init
- type: plan
- type: run # OPA, CheckMarx, Dome9, etc.
cmd: ["./security-and-policy-checks.sh"]Example: Access Control
access_control:
ci_config_update: ["team:sre"]
policies:
- tag_query: "production and compute in dir"
superapproval: ["team:sre"]
apply_with_superapproval: ["*"]
apply: ["team:sre"]
- tag_query: "production"
plan: ["team:engineering"]
apply: ["team:sre"]
- tag_query: ""
terrateam_config_update: ["team:sre"]
unlock: ["team:sre"]Example: Apply Requirements
apply_requirements:
checks:
- tag_query: "production"
approved:
enabled: true
all_of: ["team:security"]
merge_conflicts:
enabled: true
status_checks:
enabled: true
- tag_query: "staging"
approved:
enabled: true
any_of: ["team:engineering"]Gatekeeper
- type: init
- type: plan
- type: conftest
gate:
token: denied-resources
any_of: ["team:engineering"]
any_of_count: 1AI Integration & What’s Coming
Currently Available: Error Explanations
- Inline error explanations
- Guidance in natural language
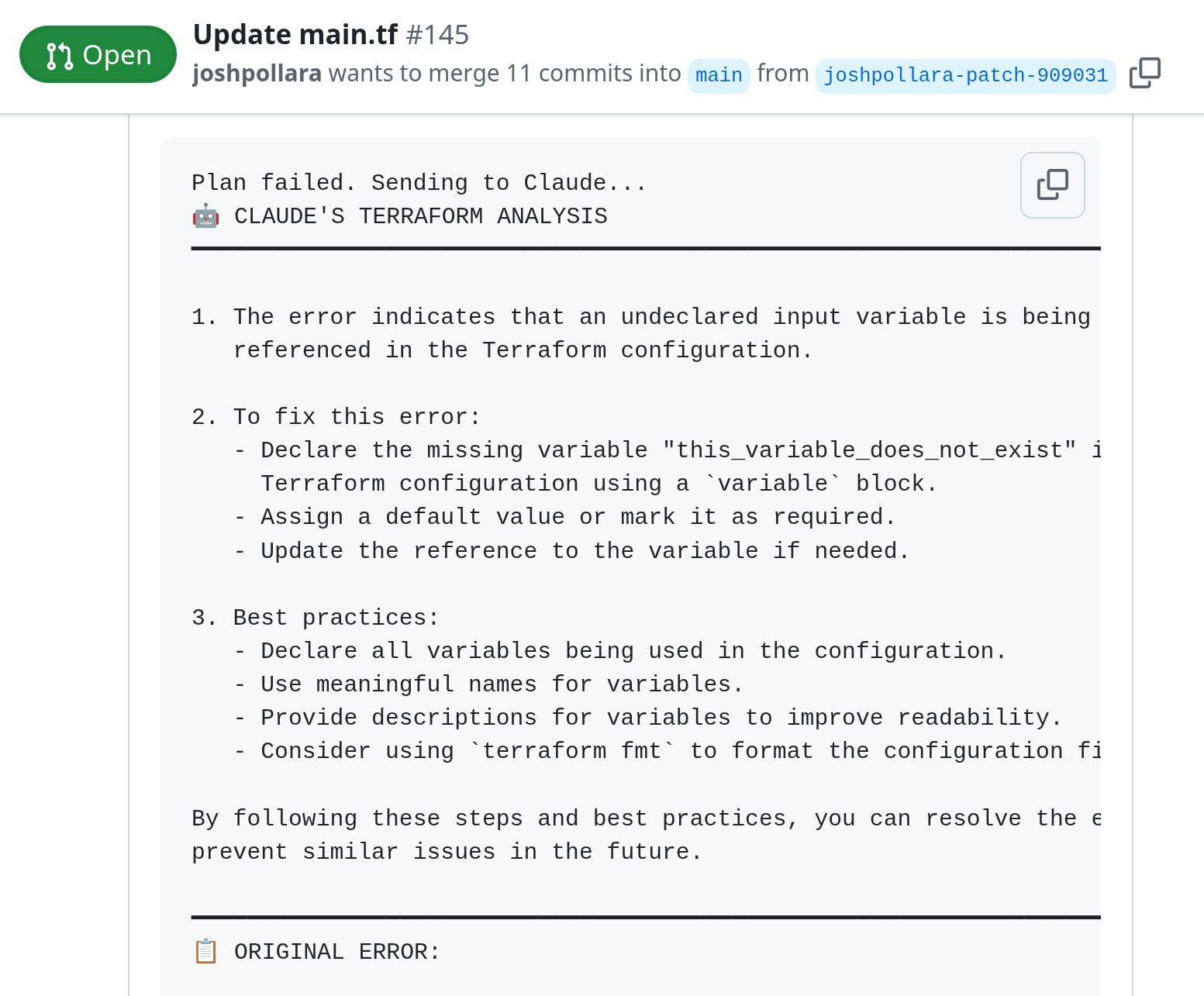
Currently Available: PR Summaries
- Summaries in PR
- Automatic change analysis
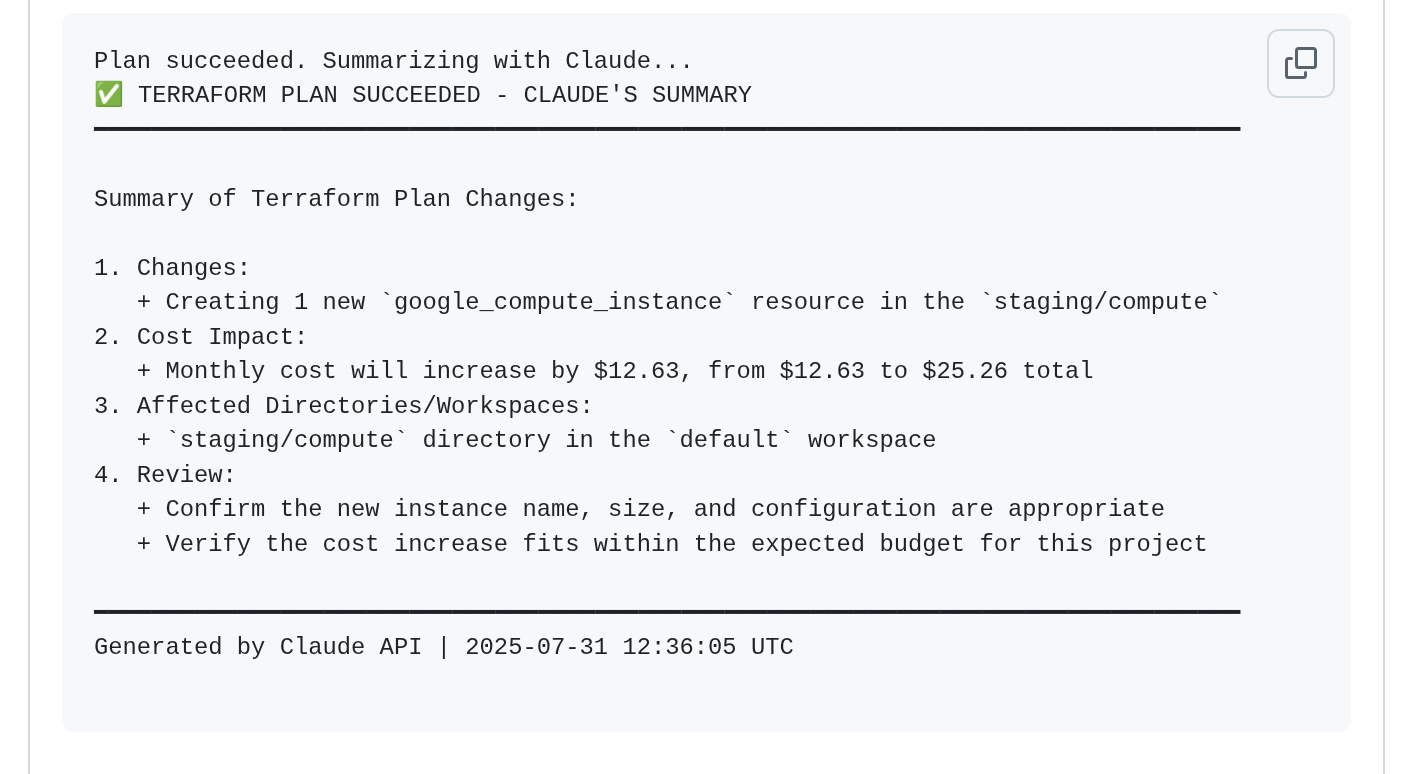
Coming Soon
Auto-generated PRs for drift remediation
Explain + suggest changes in plain English
Integration with internal knowledge bases (opt-in)