Terrateam vs. Atlantis
Atlantis started the GitOps movement for Terraform. Terrateam scales it with native GitHub integration, policy enforcement, and enterprise-ready workflows.
Atlantis inspired the GitOps era
Atlantis deserves respect. It pioneered GitOps for infrastructure, brought Terraform automation to thousands of teams, and did it as open source. For a long time, it was the only game in town if you wanted PR-based infrastructure workflows without vendor lock-in.
But pioneering technologies reveal their limitations as teams scale. When teams grew, infrastructure exploded, and monorepos became the norm, Atlantis's single-threaded execution became a bottleneck. Teams calculated they lost 15+ engineering hours per week waiting for operations to complete.
We built Terrateam not to make "Atlantis but slightly better," but because we had fundamentally different opinions about how this problem should be solved, informed by modern distributed systems thinking, deterministic concurrency, and values about what infrastructure software should be.
Built for Today's Infrastructure Teams
Atlantis introduced GitOps for Terraform. Terrateam builds on that foundation with tighter GitHub integration, a modern UI, and scalable workflows for growing teams.
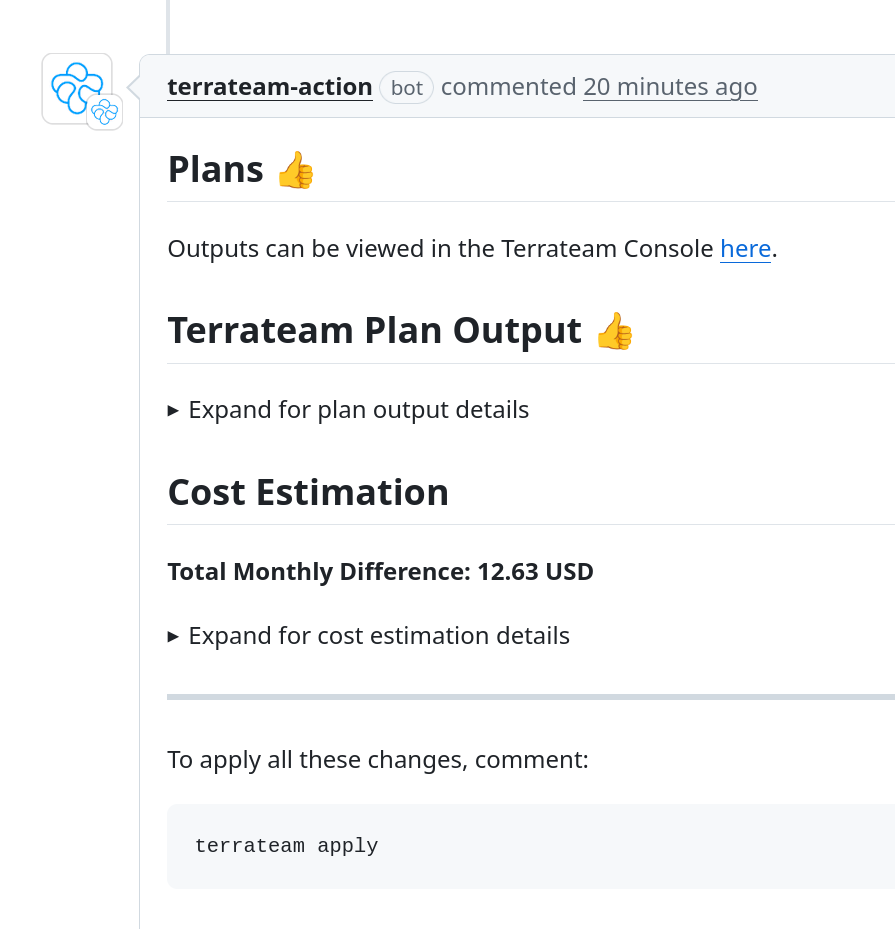
At a Glance
GitHub Integration
Terrateam
GitHub App & Actions, checks, teams
Atlantis
PR comments only
Config-as-Code
Terrateam
Highly expressive, dynamic configuration, centralized repo config
Atlantis
Hard to scale, no reuse, scattered config
Policy Enforcement
Terrateam
Built-in OPA + Apply Requirements + Gatekeeper override
Atlantis
Must build your own
| Feature | Terrateam | Atlantis |
|---|---|---|
| Multi-engine support | Terraform, OpenTofu, Terragrunt, CDKTF, Pulumi, Custom (Any CLI) | Terraform/OpenTofu-only |
| Architecture | Run many servers backed by PostgreSQL | Single binary, local DB |
| Self-hosted option | Docker-based deployment | Self-hosted only |
| Enterprise support | Yes + SLA | Community only |
| Pricing | Transparent (no usage-based fees) | Free / OSS only |
Feature Comparison Grid
| Capability | Terrateam | Atlantis |
|---|---|---|
| GitHub App Integration | Built-in | Bot-based comments |
| Approval Workflows | Granular Apply Requirements | Basic Apply Requirements |
| Config-as-Code | Expressive in-repo YAML | In-repo YAML + server flags |
| Policy Enforcement | OPA/Conftest + Gatekeeper | No first-class support |
| Audit Trail | Persistent + queryable | Not supported |
| Secrets Handling | GitHub Secrets + isolation | No simple secrets solution |
| Multi-IaC Engines | Terraform, OpenTofu, CDKTF, Terragrunt, Pulumi | Terraform/OpenTofu CLI only |
| Architecture | Horizontally scalable, DB-backed | Single-node only |
| Runners | Isolated per environment | Shared execution on server |
| Cost Estimation, Drift Detection | Native support | Requires external tooling |
| Role-Based Access Control | GitHub teams, users, roles | Requires external tooling |
Persistent Audit Trail
Every plan, apply, and decision is recorded with full visibility. Searchable, filterable, and built for compliance.
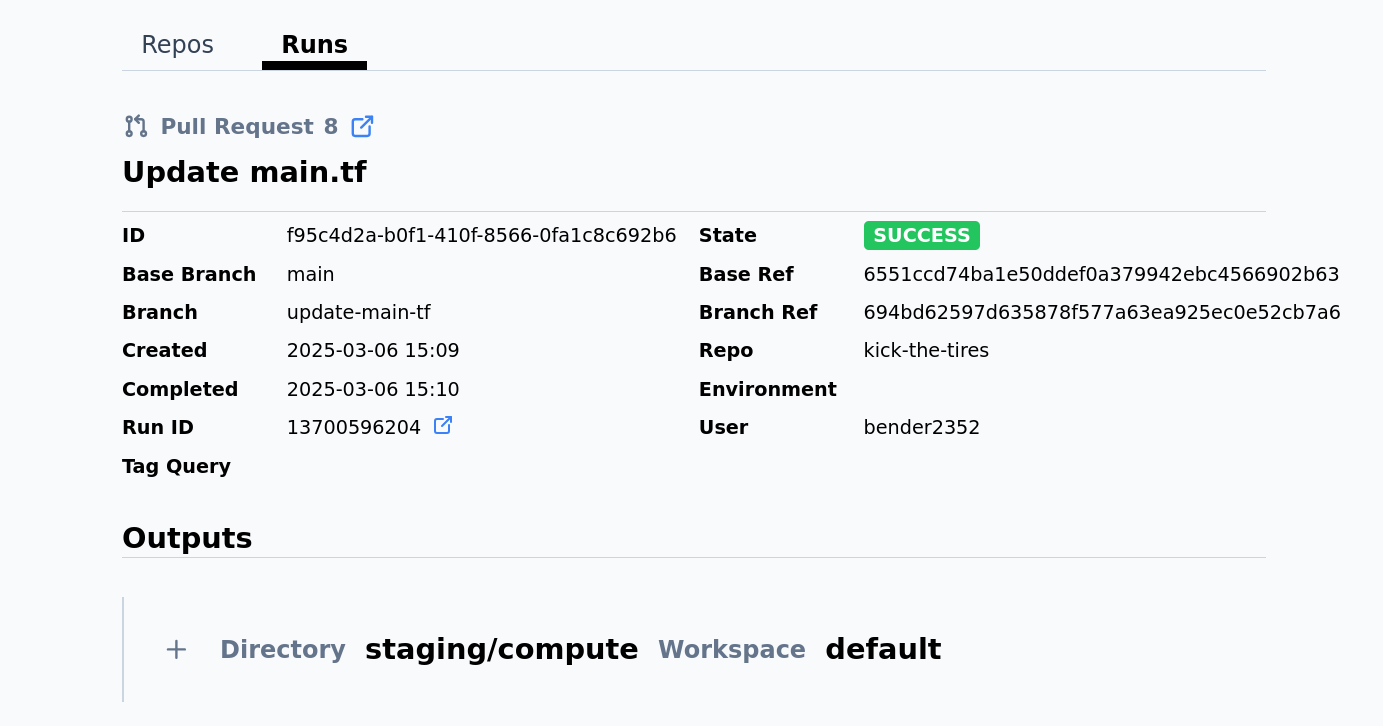
Architecture Overview
Terrateam Architecture
GitHub App integration
Persistent PostgreSQL database
Isolated runners (Docker-based)
Declarative YAML config (extremely expressive)
Scales horizontally
Atlantis Architecture
Single Go binary
Local database only
Shared execution per plan
Relies on bot comments and static config
Redis optional for locks
Atlantis is simple to set up but easy to outgrow.
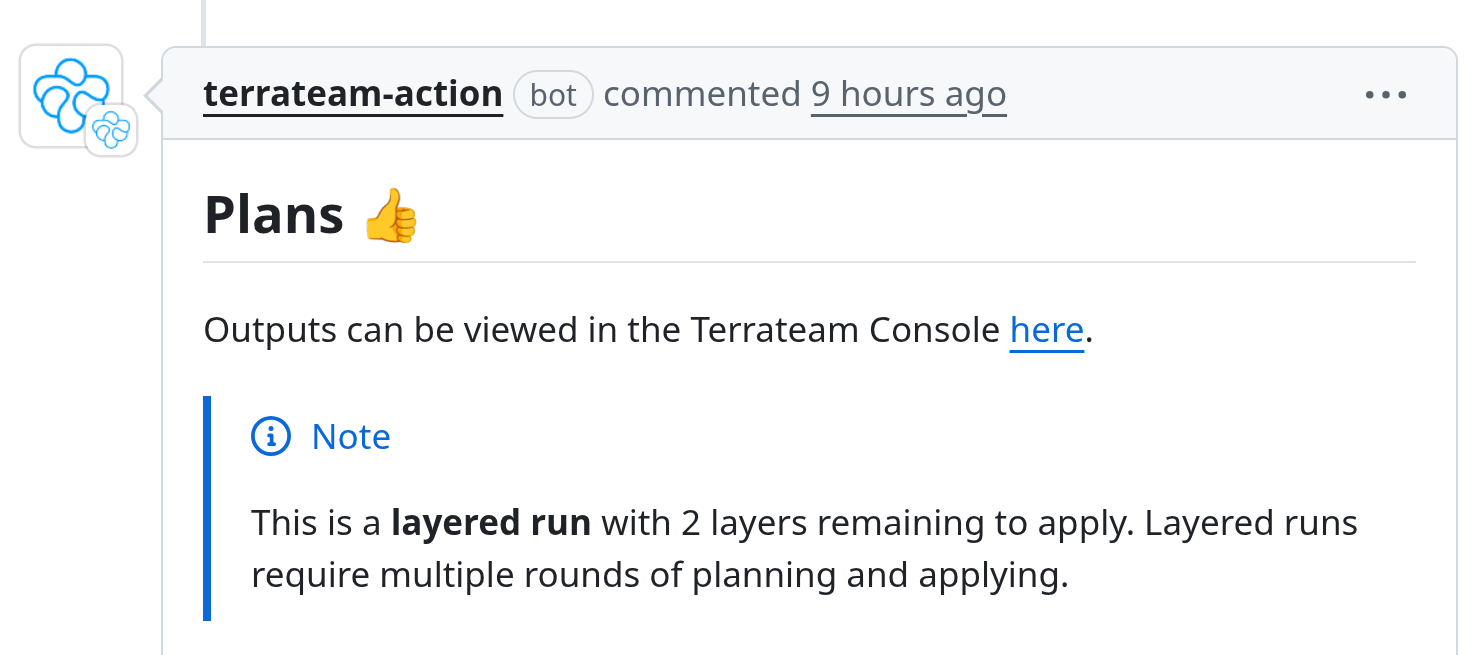
Orchestrated Layered Runs
Every plan, apply, and decision is recorded with full visibility. Searchable, filterable, and built for compliance.
Pain Points Solved
Atlantis Limitations
Hardcoded workflows
No GitHub team support
Lacks audit trail
No built-in policy enforcement
Terraform/OpenTofu-only
Shared runners
Limited UI
Terrateam Solutions
Highly expressive in-repo configuration file
Native GitHub App with team approvals
Persistent database
OPA + Apply Requirements + Gatekeeper built-in
Terragrunt, OpenTofu, CDKTF, Pulumi, Custom CLI all supported
Isolated, per-operation runners
Checks, statuses, and GitHub-native integration
Use Case Comparison
| Scenario | Terrateam | Atlantis |
|---|---|---|
| Engineering org w/ 20+ modules, multiple teams | Built for this | High maintenance |
| Team migrating from Atlantis | Smooth transition with hands-on support | — |
| Platform team w/ strict audit + policy | Supported | Limited controls, no policy engine |
| Using Terragrunt, OpenTofu, CDKTF, Pulumi, or Custom CLI | Native | Challenging |
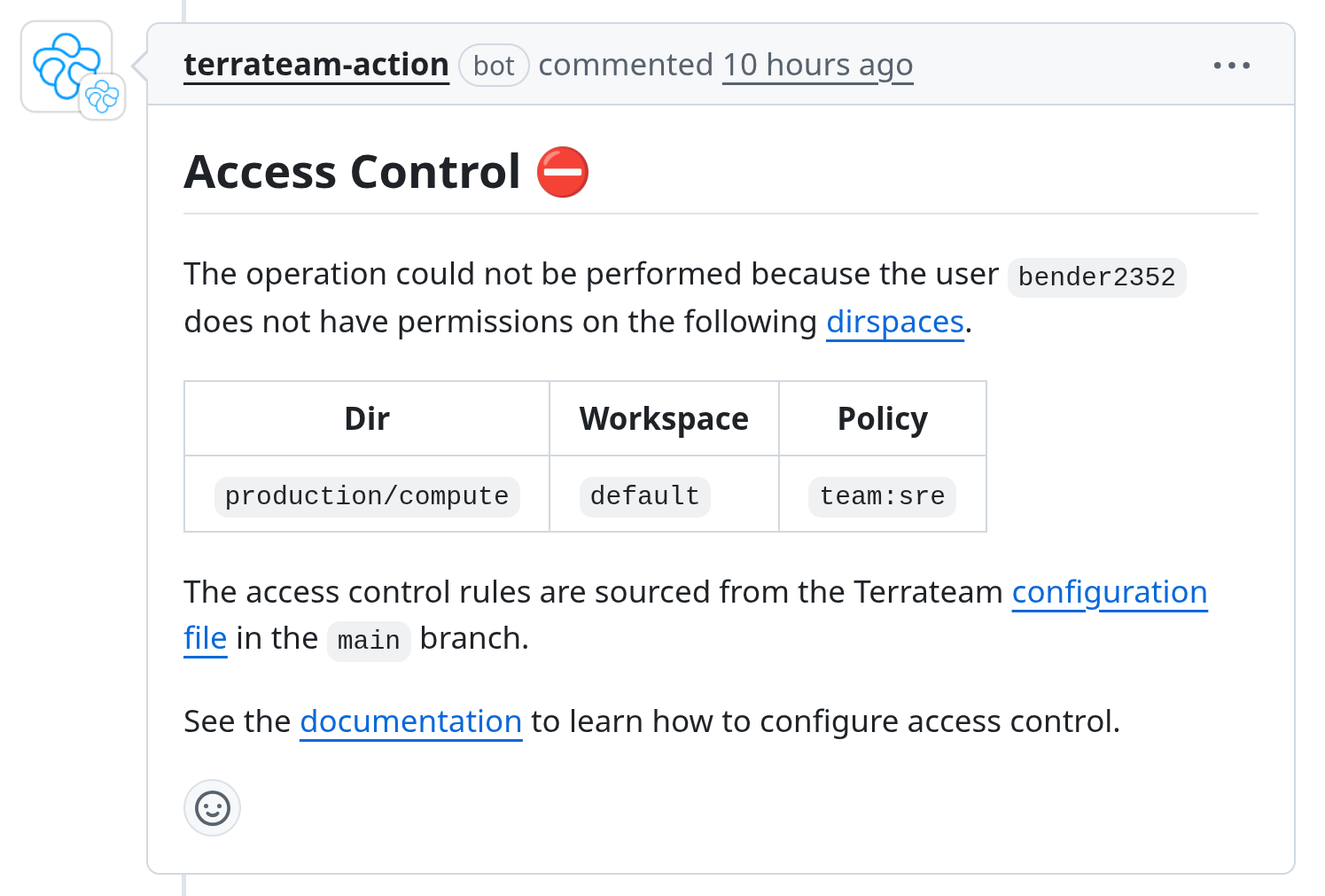
Built-in Policy Enforcement
Enforce policies and approvals before infrastructure changes are applied. Terrateam includes native support for OPA, Conftest, and GitHub-based apply requirements and access controls. No extra setup needed.
"We were hitting the limits of what Atlantis could handle. Terrateam gave us structure, approvals, and policy without rebuilding everything."
Patients Know Best Case Study
Atlantis introduced GitOps for Terraform. Terrateam brings it to the enterprise.
If you're hitting the limits of comment bots and static configs, it's time for a GitHub-native alternative built to scale.