Scanning Terraform Plans with Checkov
Terrateam integrates with Checkov, a popular tool for scanning infrastructure as code, to help you detect and prevent common misconfigurations in your Terraform plans. By running Checkov against your Terraform plans as part of your Terrateam workflows, you can identify potential issues before they are applied to your infrastructure, ensuring better security and compliance.
What is Checkov?
Checkov is an open-source tool that scans infrastructure as code (IaC) files, such as Terraform configurations, to identify misconfigurations, security issues, and compliance violations. It provides a comprehensive set of built-in policies and checks based on industry best practices and compliance standards like the CIS Benchmark, HIPAA, and PCI-DSS. Checkov can be integrated into your CI/CD pipeline to automatically scan your Terraform plans and provide feedback on potential issues, helping you catch and fix problems early in the development process.
Configuring Checkov
To integrate Checkov with Terrateam, you need to configure a custom workflow in your Terrateam configuration file (.terrateam/config.yml).
Here’s an example configuration that runs Checkov against the generated Terraform plan:
workflows: - tag_query: "" plan: - type: init - type: plan - type: run cmd: ['checkov-wrapper'] capture_output: trueIn this configuration:
- The
initandplansteps generate the Terraform plan as usual. - The
runstep executes thecheckov-wrapperscript, which calls thecheckovbinary with the generated Terraform plan file. - The
capture_outputoption is set totrueto include the Checkov output in the Terrateam plan results.
Scanning Terraform plans
When a Terrateam plan operation runs with Checkov integration enabled, the following steps occur:
-
Terrateam generates the Terraform plan file.
-
Checkov is executed against the generated plan file, scanning for misconfigurations and policy violations.
-
If Checkov detects any issues, it returns a non-zero exit status, causing the Terrateam plan operation to fail.
-
The Checkov output, including details about the identified issues, is captured and included in the Terrateam plan results.
-
If the plan passes the Checkov scan without any issues, the Terrateam plan operation succeeds, and the plan can be reviewed and applied as usual.
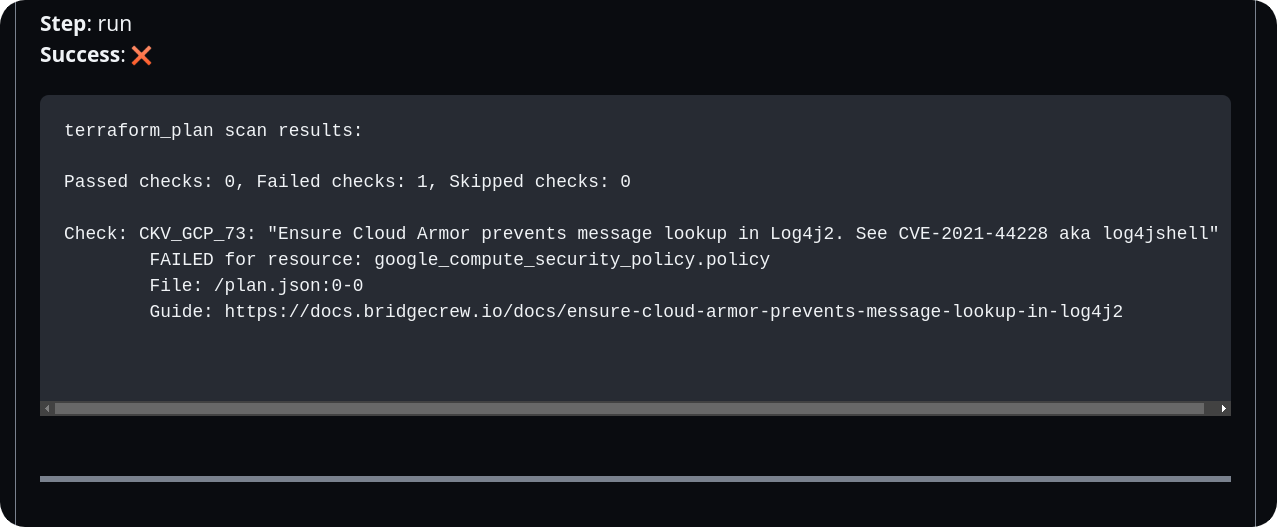
Here’s an example of a Terrateam plan failing due to a Checkov scan detecting misconfigurations:
Customizing Checkov options
Checkov provides various configuration options that can be customized using environment variables. You can find the full list of Checkov configuration options here.
Here’s an example of how to skip a specific check using the CKV_SKIP_CHECK environment variable in your Terrateam workflow:
workflows: - tag_query: '' plan: - type: env name: CKV_SKIP_CHECK cmd: ['echo', 'CKV_GCP_73'] - type: init - type: plan - type: run cmd: ['checkov-wrapper'] capture_output: trueIn this configuration:
- The
envstep sets theCKV_SKIP_CHECKenvironment variable toCKV_GCP_73, indicating that the specific check with IDCKV_GCP_73should be skipped during the Checkov scan. - The subsequent steps (
init,plan, andrun) are executed as usual, with Checkov using the specified configuration options.
